Why can ignoring notifications be costly for businesses? What risks do warnings hide? Learn how to respond to them correctly and why quick intervention strengthens your digital security defenses.
Every activity we perform on a computer leaves a trail. For businesses that handle sensitive papers, financial information, and databases, even a modest warning from Mac alerts can indicate a major hazard. Many users, noticing unexpected notifications on their Mac alerts, tend to ignore them. After all, they consider them to be minor technical glitches. However, these signals may indicate that your data is already at risk.
Key Highlights:
- Early Indicators of Threats
- The Role of the Human Factor
- Risks of Ignoring Mac Alerts
- Corporate Data Protection Through Timely Response
- Preventive Measures
Early Indicators of Threats. Unexpected Mac Alerts Notifications
The macOS operating system is designed to alert users to suspicious activity in real time. When you see a message such as your screen is being observed, it is by no means a coincidence. It is a signal that some program or process has gained access to screen recording or an external connection. One that is capable of intercepting information. The business environment is particularly vulnerable to such threats. This is because corporate data is a tempting target for hackers. Ignoring messages similar to Why is my Mac alert showing your screen is being observed? opens up opportunities for spyware:
- To collect data;
- To intercept passwords and business correspondence;
- To monitor employee actions in real time.
A reliable approach involves:
- Immediate system verification;
- Identification of processes that have been granted access rights;
- Threat level assessment.
This is where cyber hygiene becomes a key tool. Regularly updating macOS and controlling application permissions. Using specialized solutions that help identify and neutralize suspicious processes. All of this can save your business from data leaks.
Gradually, there are more and more scenarios where a message on the Mac alerts screen is a warning about a leak or an active hack. By ignoring them, the company is actually giving attackers more time to manipulate. In such cases, the right strategy is not to ignore the signal. Treat every system warning as an indicator that needs to be diagnosed.
If the warning appears repeatedly or for no apparent reason, this is a reason to check permissions and review the list of active processes. If necessary, use proven instructions to fix the problem. If you notice alarming notifications such as “your screen is being observed” or do not understand “how to turn off your screen is being observed,” then you should not only respond correctly, but also know how to get rid of potentially harmful processes. In this context, it is useful to familiarize yourself with practical instructions, including Moonlock’s steps to take, which explain in detail how to safely disable unwanted screen access and regain control of the system.
It will be a very useful resource for you if you want to act quickly and competently without risking your business data. Once the system has been cleaned, don’t just remove the problem, but also analyze it. That is, find out how it arose and which applications gained access. Also, check whether there are any other hidden threats. Only a comprehensive approach can ensure that the threat is completely neutralized.
The Role of the Human Factor. Privacy Concerns

Most corporate data leaks start with human negligence, not sophisticated hacker attacks. Employees often don’t take privacy concerns seriously. They think system messages are trivial. This mistake opens the door to attacks.
When the threat comes from within
Sometimes, installing seemingly useful applications that request extended permissions opens the door to leaks. An employee who clicks “allow” without thinking twice can give a malicious program full access to their screen, camera, microphone, and corporate files. Such scenarios are particularly insidious. They look like legitimate work activity. When an employee installs a program that has been recommended to them, the risk seems minimal.
However, malicious software today is often distributed under the guise of:
- Productivity utilities;
- Communication tools;
- mac alerts optimization tools.
It may request access rights to functions that, at first glance, are not related to the main task.
Internal risks are further complicated by the fact that they are rarely immediately noticeable. Malicious software can run in the background for weeks without raising suspicion. Meanwhile, it collects data, saves screenshots, and tracks user activity. This allows attackers to create detailed profiles of corporate systems and find vulnerabilities. Sometimes they can even obtain passwords or access tokens to internal services.
As a result, the company faces a strategic threat. Attackers gain insight into:
- Internal processes;
- Business structure;
- Partnerships.
All of this can be used for more sophisticated attacks. In particular, targeted phishing campaigns or blackmail. That is why internal control, auditing of installed software, and restricting user rights are critical elements of corporate cybersecurity.
External risks. Phishing and targeted attacks
Phishing emails that offer to download “security updates” or “plugins for Mac” are often nothing more than spyware installations. That is why you should take system messages seriously. If your Mac alerts warns you about screen recording, don’t just close the message, but understand why it appeared.
The habit of ignoring even the smallest security risk signals creates a dangerous scenario of cumulative risk. When one employee ignores a warning, another installs a program without checking it. And a third works from an unsecured Wi-Fi network. And then the company becomes vulnerable for no apparent reason. As a result, a single successful attack is enough for the leak to lead to legal consequences and fines for violating data protection rules.
Current legislation in many countries sets strict requirements for the processing and storage of personal data. A delayed response to an incident that began with a simple system warning can result in fines of millions of dollars. Therefore, paying attention to mac alerts notifications is also a legal requirement.
5 Shocking Risks of Ignoring Mac Alerts
5 Shocking Risks of Ignoring Mac Alerts are:

1. Data Theft
If you ignore alerts, malware can exfiltrate business files, financial data and passwords. Even a small breach can result in millions of dollars in harm or loss of intellectual property. It is imperative to act quickly and that you do not allow attackers to gain persistent access.
2. Employee Monitoring Exposure
Spyware or unwanted programs can use employees who steal identity or information. Perhaps they don’t care about privacy, but their spying is criminal. Losing the trust of an employee can create a legal and ethical dilemma for your company. Alerts should be taken seriously.
3. Unauthorized Access
Malware could give malicious apps complete computer access. Control of your screen, microphone and camera means that you control access to systems and spying by contextualizing hesitation through can sometimes is malicious. Malware could also take that access for itself, you are playing with fire. Limiting or finding what apps have access to your Mac reduces a substantial amount of risk.
4. Legal & Compliance Issues
Ignoring security breach assumption process can expose the company to penalties such as GDPR (fines for breaching data protection laws are going to be large). GDPR fines may or not be applicable relative to a breach of sensitive customer or employee data that can not only lead to litigation against the company but also can them under regulatory scrutiny. Having a solid incident response protocol will demonstrate compliance monitoring and help protect the business.
5. Reputation Damage:
Data breaches as consequences of overlooked alerts can damage your brand, loss of client equity or distressed long-term client relationships. Potential for negative publicity can question the company’s brand and risk slowing future revenue growth with prospective clients and partners. Managing alerts and adopting an aggressive incident response shows the stakeholders of your company that you take Security seriously.
Optimizing Battery Life as a Cover for Malicious Processes
An interesting but dangerous trend in recent years has been to use the topic of productivity to hide spyware tools. Many malicious programs masquerade as utilities for optimizing Mac.” The latter promise to optimize battery life, speed up the system, or clean up memory, etc. Under the guise of a legitimate service, they obtain extended permissions. This includes the ability to take screenshots or transfer screen content to external servers.
Some of these utilities even imitate Apple’s official style. That is, they create the impression of being safe software. They may contain fake certificates or use social engineering tactics. That is, they convince users to grant full access in order to supposedly improve energy consumption or protect the battery from degradation. In reality, they hide modules that secretly record the screen and collect keystrokes. Then, they transfer all this to external servers, where the data is analyzed and sold to competitors or criminal groups.
Corporate Data Protection Through Timely Response
There are specific steps you should take immediately after receiving an unexpected alert.
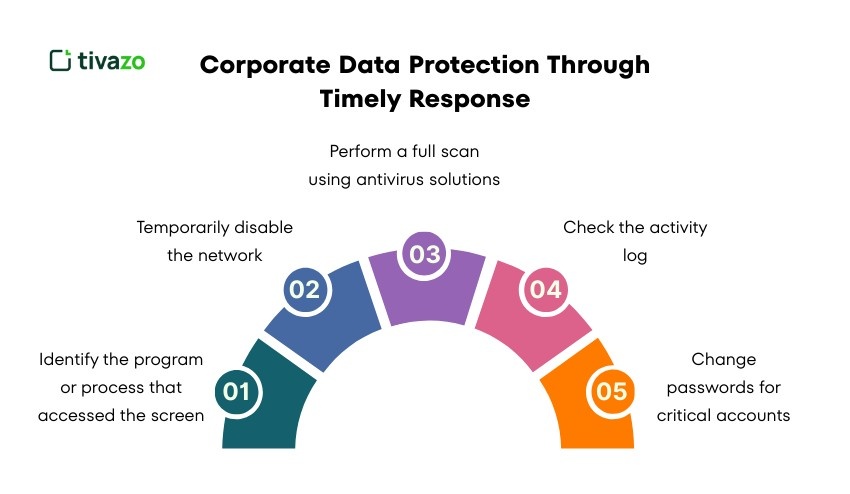
- Identify the program or process that accessed the screen.
- Temporarily disable the network. This will limit data leakage.
- Perform a full scan using antivirus solutions that specialize in mac alerts.
- Check the activity log and application permissions.
- Change passwords for critical accounts.
Document incidents. Even if the problem has been resolved, records of when and under what conditions the message appeared, what actions were taken, and what files may have been opened will help assess the real scale of the threat.
Many companies neglect post-incident analysis. However, it is precisely this analysis that allows you to better prepare and prevent similar situations in the future.
The faster a company responds, the less chance attackers have to complete their attack or steal sensitive data.
Preventive Measures: Creating a Culture of Cybersecurity
No technology can replace human vigilance. Therefore, training employees, developing internal policies for using mac alerts, and installing only verified apps all contribute to creating an environment where unexpected warnings are not ignored but are taken as an important signal to take action.
Regular updates. Permission control
Updating mac alerts and software components is the first line of defense against attackers. Permission control allows you to quickly spot anomalies. Specifically, this refers to control over:
· Screen recording;
· Access to the camera and microphone.
Monitoring tools. Backups
Backups and monitoring of suspicious activity not only help restore data. They also help you understand what happened. Log analysis systems allow you to detect unauthorized actions more quickly.
Training
A cybersecurity culture cannot exist without regular training sessions. During these sessions, employees:
- Learn about real-life attack cases;
- Practice recognizing fake messages;
- Learn to distinguish genuine mac alerts warnings from malicious fakes.
The more attention a company devotes to prevention, the less likely it will be forced to deal with the implications of a genuine breach.
After all, the expense of educating and adopting regulations is far less than the damages caused by the leakage of important company data.
Conclusion
Ignoring unexpected mac alerts warnings is much more than a minor mistake. It is a risk that can harm both your company’s brand and its bottom line. The keys to protecting your company data include timely response, attention to detail, the deployment of trusted tools, and the establishment of a cybersecurity culture.
Remember that each warning is an opportunity to avert a problem before it causes irreversible damage. In an era when digital data privacy is becoming one of the most precious business assets, disregarding these signals means knowingly opening the door to cyber spies.




