Digital space in 2025 is going to have the greatest cybersecurity threats ever, leaving a gap for system vulnerability assessment. More than 21,500 new vulnerabilities were published during the first half of this year alone – 18% more than those of last year, and 38% were of High or Critical severity. The average cost of a data breach in the world stands at 4.88 million dollars, and the losses incurred due to cybercrime are expected to go beyond 14 trillion dollars by the year 2028. None of the 300 new CVEs every day and exploits being immediately weaponized has made the necessity of proactive system vulnerability evaluation more urgent.
Any unpatched vulnerability is a possible point of attack. The truth is shocking – 72 percent of business leaders note that there is growing attack sophistication, and 61 percent of companies have encountered at least one breach related to the cloud over the last year. More than 20% of all breaches are now vulnerability exploitation, almost covering phishing and credential theft as an important attack strategy.
It is a starting point of a data-driven response: in order to protect the digital ecosystems and reduce compliance, all enterprises should focus on systematic system vulnerability assessment at the network, endpoint, and cloud levels.
The Importance of System Vulnerability Assessment
A system vulnerability test determines the vulnerabilities that can be exploited, misconfigurations, and outdated parts before attackers discover them. As the number of disclosed vulnerabilities in the world is expected to reach more than 50,000 in 2025, the idea of patching and exposure reduction requires a sound evaluation.
As opposed to reactive strategies, it is a pattern that provides organizations with early visibility of vulnerabilities, allowing them to monitor risks in terms of severity, criticality of assets, and probability of exploitation. Applying the principles of risk-based vulnerability assessment enables the teams to deploy security resources most effectively, reducing the threats with high impacts first.
Also, the move to hybrid work increased attack surfaces. The majority of companies have shifted to zero-trust models now to fight lateral movement and insider threats management up to 86 percent. This will go hand in hand with proactive IT infrastructure assessment, where it is viewed as real-time scanning and continuous testing to ensure that the systems are robust to the changing attack patterns.
Vulnerability Situation Globally
The cybersecurity landscape in 2025 is indicative of growing pressure in the context of continuous defense. Recent data highlights –
- 50,000 estimated CVEs per year, a record upsurge.
- OS, web applications, and IoT 133+ new vulnerabilities/day.
- 61 percent of cloud users report having been breached at least once a year.
- IoT: 70 percent of the used devices are still at risk of remote exploits.
Ransomware attacks on backup repositories have increased to 96 percent today.
These tendencies explain why vulnerability management tools integrated are the backbone of the current cyber defense model. Automated risk scoring and constantly verifying it is an essential countermeasure now that the weaponization of many exploits has been possible within hours.
Companies that apply AI to conduct vulnerability scans have seen a 35 percent decrease in their patch time and, on average, have seen a 108-day faster incident detection time. The ability to adapt to threats efficiently and quickly through flexibility defines successful models of defense nowadays.
Key Elements of Successful System Vulnerability Assessment.
A comprehensive, data-driven system vulnerability assessment contains 5 key steps:
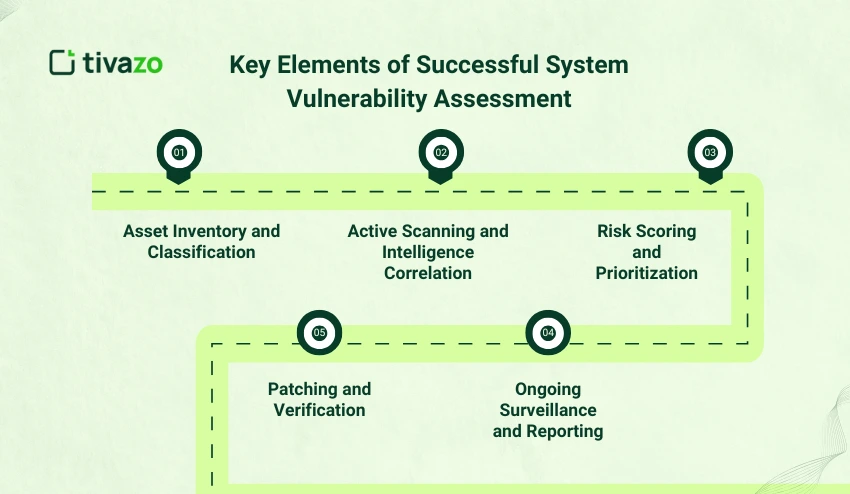
- Asset Inventory and Classification – Identifying servers, endpoints, API, and devices connected to create a complete technology baseline.
- Active Scanning and Intelligence Correlation – With modern vulnerability management tools, one can determine old software and unpatched vulnerabilities.
- Risk Scoring and Prioritization – The use of contextual data to measure risk as a vulnerability assessment, which is important in the probability and impact of exploits.
- Patching and Verification – Implementing timely updates and mitigation, as well as configuration hardening of all high-risk assets.
- Ongoing Surveillance and Reporting – It is necessary to take continuous surveillance of new CVEs by utilizing automated feeds and external databases such as KEV, maintained by CISA.
These levels improve operational preparedness, especially in controlled businesses wherein compliance management and security guidelines like NIST, ISO 27001, and the EU Cyber Resilience Act demand evidence of organized vulnerability management.
Scaling and Automating Smart Defense
Enterprises that operate in large-scale environments are relying on automation in IT infrastructure assessment models. Research indicates that automation and AI on security processes help to save up to $3 million on each breach, and containment time decreased by 73 days.
The machine learning models used in vulnerability management tools are now able to detect likely exploit paths and rank them in terms of business impact. Combination with SIEM and SOAR systems deepens proactive response – minimizes downtime expenses, which means an average of UDS 53,000 per ransomware hour.
Automation does not remove human control – it increases it. The analysts can see more, and the manual work is lessened, ensuring quick and tested remediation.
Human Failure and Critical Vulnerabilities
Human error is still a cause of 88% of cyber incidents despite the level of advancement in technology. Broken access control, cross-site scripting (XSS), and SQL injection are still the most common vulnerabilities that are clustering the CVE charts of 2025. Such weaknesses emphasize the need to implement safe code and system security testing during software lifecycles.
Ongoing evaluation of the system weaknesses deals with the configuration vulnerabilities and process vulnerabilities. It promises not only the capability to resist new zero days but also old vulnerabilities, as much as over a decade, such as those that have been used recently in legacy Internet Explorer bugs.
Vulnerability Evaluation in the Future
The future trend of the industry in 2025 and beyond is focused on real-time, unified risk prediction. According to Gartner, the global cybersecurity expenditure will exceed an expenditure of more than 377 billion by the year 2028, and the bulk of the latest investment is expected to be channeled into risk-based vulnerability assessment solutions.
The artificial intelligence systems are already charting vulnerabilities to probable exploit timelines, which dynamically change priorities on patches depending on the probability of threats. This feedback loop allows security teams to continuously refine their approach, adjusting strategies as new data emerges and threats evolve.
Cloud native defense software conducts continuous scans, which makes system security and compliance testing a process that is continuously ongoing and not a yearly compliance checklist.
The next evolutionary step is the rapid implementation of the principles of Security-as-Code when testing becomes an integral part of CI/CD pipelines. The vulnerabilities will not be the external subject of audit any longer – they are integrated into the day-to-day IT lifecycle management.
Strategic Organizational Advantages
Implementation of an organized system vulnerability test provides quantifiable results that have a direct effect on business continuity:
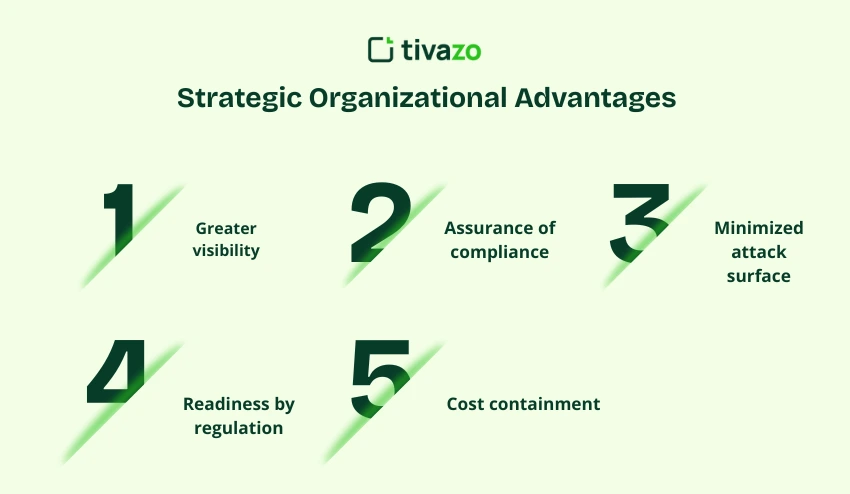
- Greater visibility – Perfect knowledge of system-level exposures and misconfigurations.
- Assurance of compliance – Improved adherence to such frameworks as NIST, SOC 2, and ISO.
- Minimized attack surface – There should be an elimination of the outdated endpoints and revoked credentials.
- Readiness by regulation – Accelerated audit of new standards like CISA.
- Cost containment – Pre-breach Risk reduction to prevent average incident costs.
These are not just security benefits but go much further in terms of creating stakeholder trust, which safeguards brand equity and shareholder confidence and informed decision-making against reputational loss.
How Qualysec Technologies Can Help You
Qualysec Technologies is a leader in the world of cybersecurity solutions. It deals with vulnerability assessment of a system and provides process-based testing to all enterprises globally.
Services
Penetration testing, security audits, vulnerability assessment, and IT infrastructure assessment
Why Qualysec is the Best

- Proven Approach – All the evaluations at Qualysec are based on a time-tested and step-by-step approach that exceeds the quality of the industry. This process identifies problems correctly, prioritizes them to be dealt with fast, and generates easy-to-follow records of compliance.
- AI + Human – The tools used by Qualysec themselves are a combination of intelligent AI analytics and manual inspections, which makes them very precise and clear. All security tests have a fixed sequence: identification of the scope, simulations, risk classification, and assurance of repairs. This approach verifies not only the fixes but also the problems with greater confidence than the regular scans.
- Global Compliance – The global team of Qualysec is guided by the best standards, such as OWASP, NIST SP 800-115, and ISO 27001, tailoring the work to each of their clients instead of working with a pre-developed automation. They provide transparent reports using a live dashboard so that managers and technical individuals can view cyber risk and its impact on the business.
- Array of Solutions – Since it is assumed that the number of other 50,000+ vulnerabilities will occur in 2025, businesses are using the risk-based tests offered at Qualysec to secure the hybrid, IoT, or cloud systems. Their systems and techniques can ensure they leave every endpoint, API, and service resilient to novel attack patterns.
Qualysec has a reputation based on process-based testing. Professionals verify all the results, thus only actual exploitable issues appear in the finished report. This eliminates false alarms and maintains efficient fixes.
Register with Qualysec Technologies today – defend all levels of your systems with step-by-step vulnerability assessments designed to be accurate!
Conclusion
A vulnerability assessment of the system will play a major role in ensuring that modern companies are safeguarded against increased and more innovative cyberattacks. The ever-changing threat world of 2025, where security issues are found and ranked all the time, will allow companies to fix them promptly and maintain high levels of defense. This initiative approach of system vulnerability assessment reduces risk, safeguards sensitive information, and satisfies more stringent global regulations. Risk-based systematic assessment helps companies to be resistant to increasing threats. It is necessary to concentrate on step-by-step checks that have proven their efficiency to prevent new methods of attacks and to ensure the future security of IT systems.
Own your security nowadays and demand a complete system vulnerability analysis by Qualysec Technologies and be ahead of the evolving cyber threats!